- RDS Instances - MySQL, PostgreSQL, MariaDB, Oracle, SQL Server databases
- Aurora Clusters - Including cluster members and read replicas
- ElastiCache Clusters - Redis and Memcached deployments
- Lambda Functions - Serverless functions with complete configuration
- Multi-Region Support - Discover resources across all your specified AWS regions
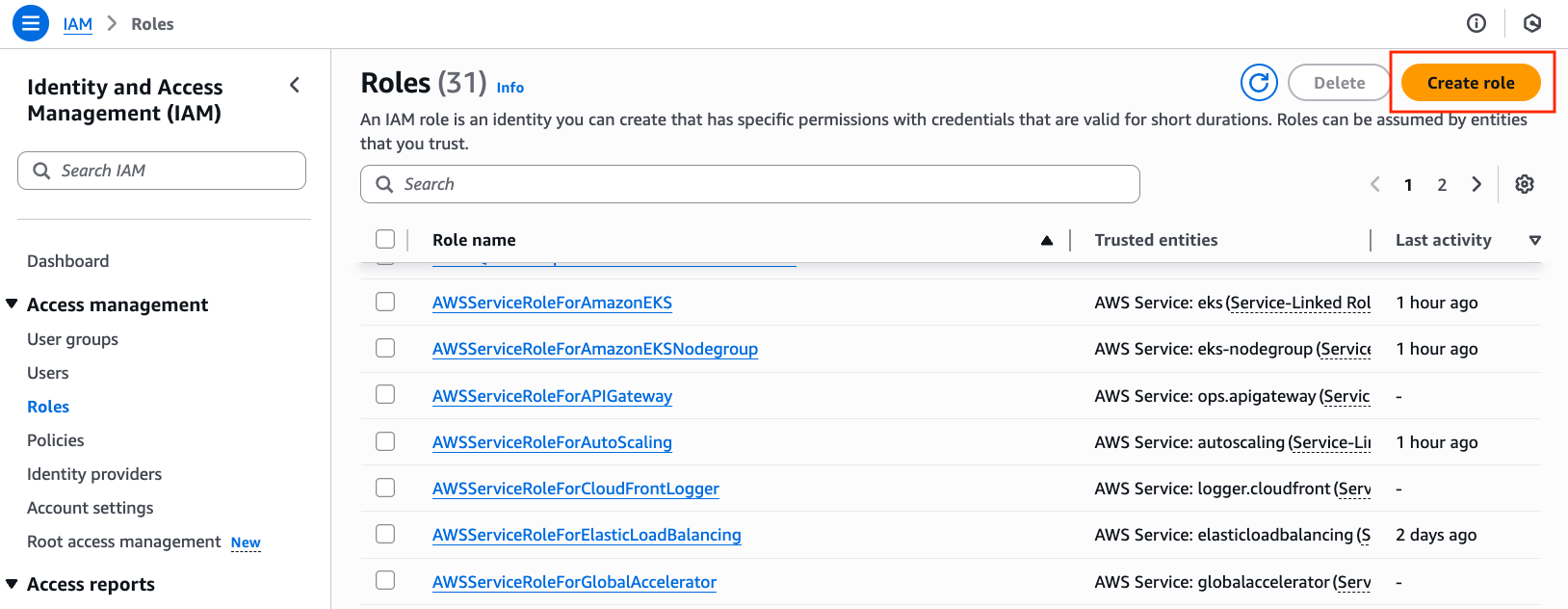
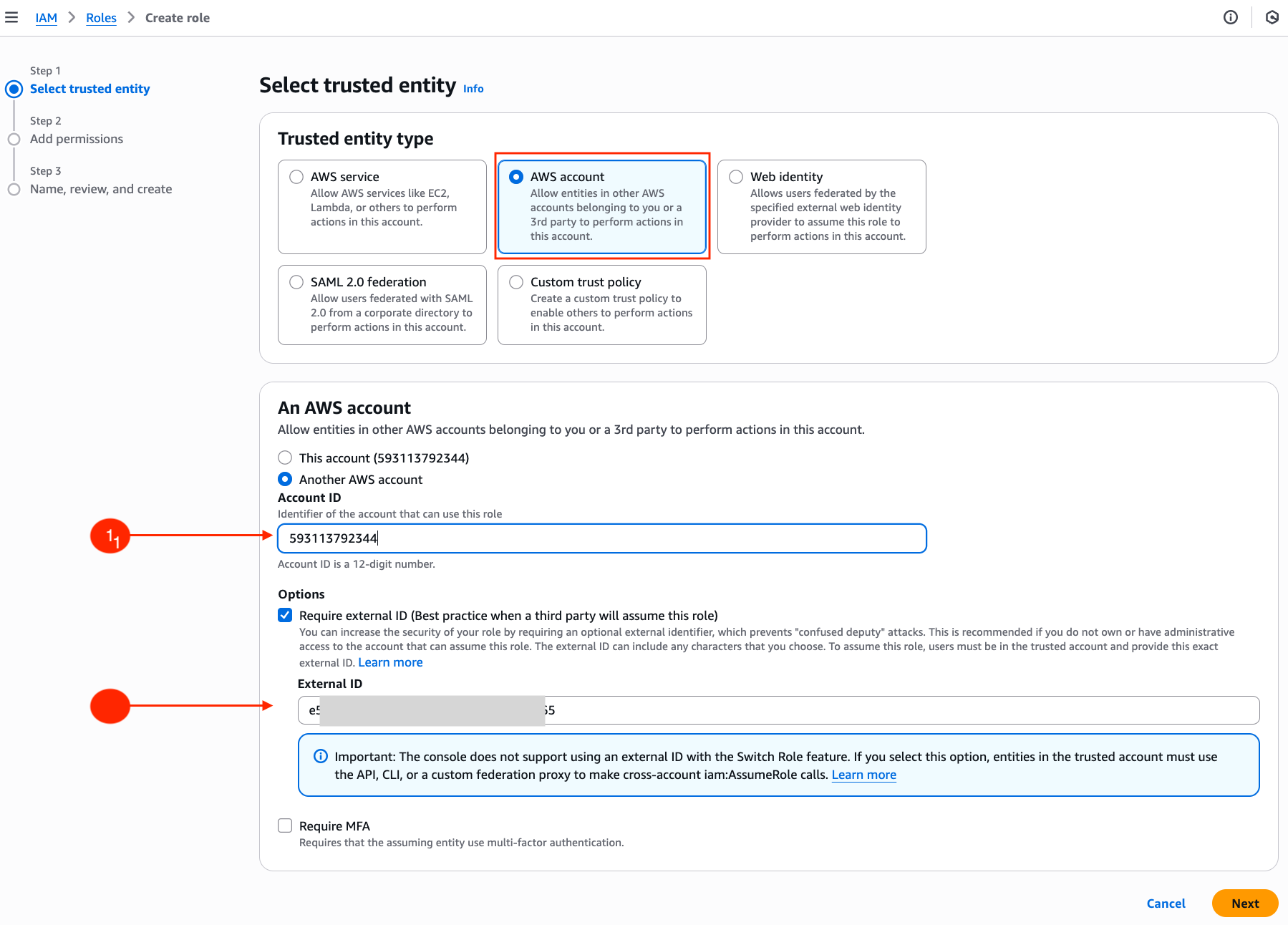
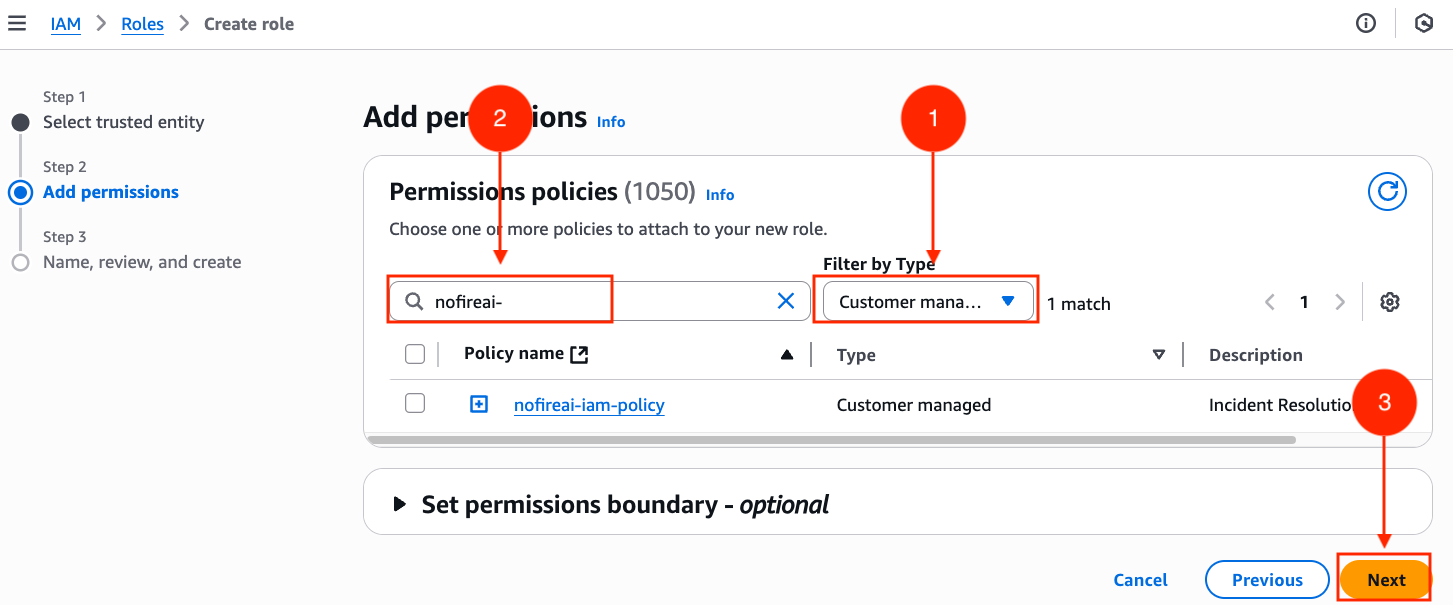
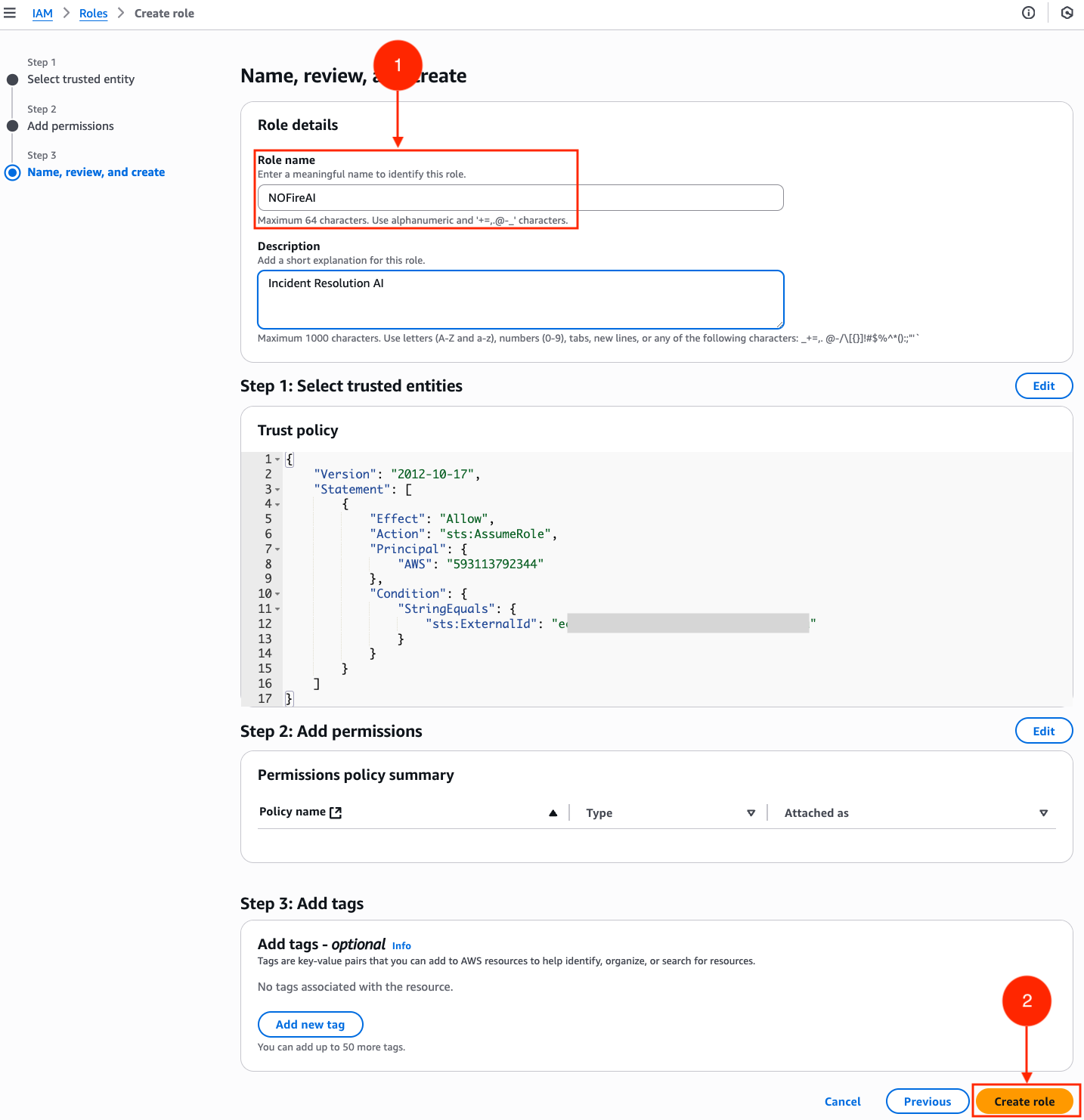
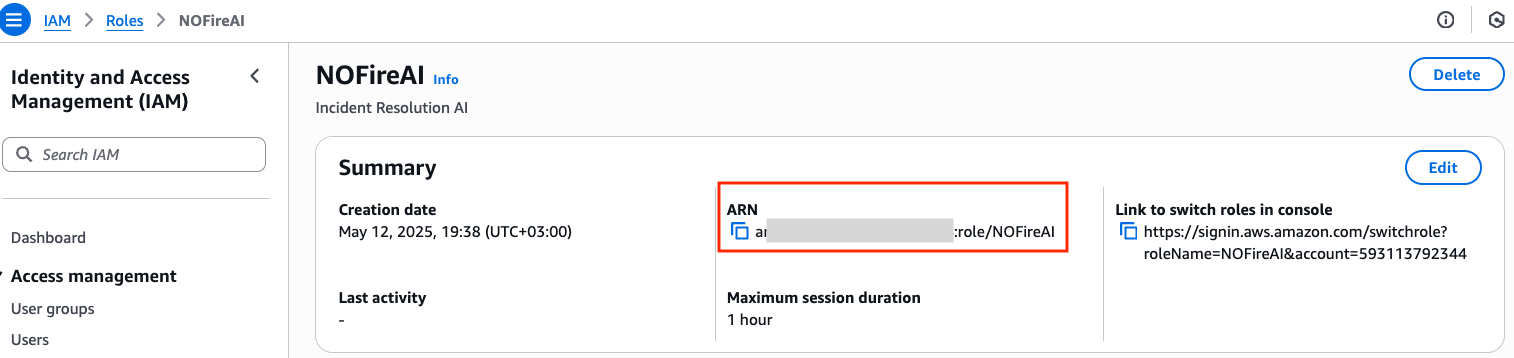
Step 1: Create IAM Role
Navigate to AWS IAM console
Navigate to AWS IAM console
Alternative: Create role using AWS CLI
Alternative: Create role using AWS CLI
For automation or scripting, you can create the IAM role using the AWS CLI:
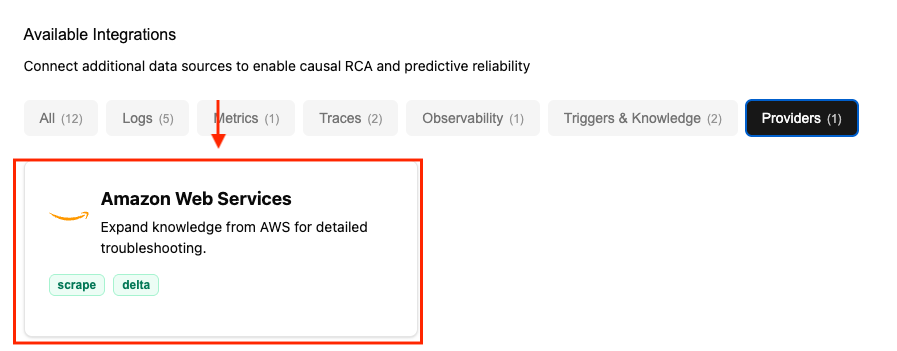
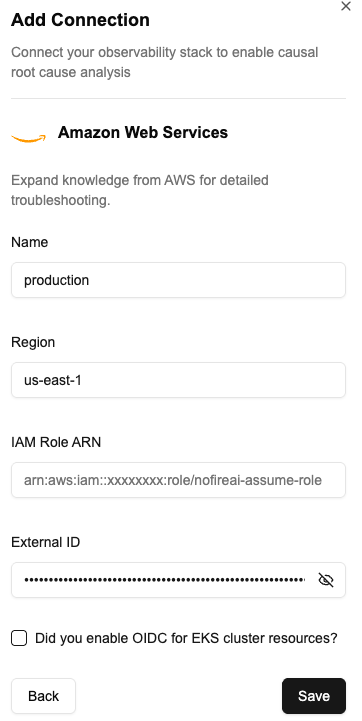
Step 2: Add AWS Connection to NOFire AI
Navigate to the Connections Tab
Navigate to the Connections Tab