Overview
MCP API tokens provide read-only access to your NOFire AI data for IDE integrations (Cursor, Claude Desktop) and developer tools. They let you query production Knowledge, assess deployment risk, and investigate incidents - all without dashboard switching. What MCP tokens can do:- Query production entities and services
- Assess deployment risk for code changes
- Analyze blast radius and dependencies
- View change history and recent deployments
- Investigate incidents and service relationships
- Modify production infrastructure
- Trigger deployments or rollbacks
- Change system configurations
- Execute commands in clusters
Generating an MCP API Token
Navigate to Administration
API Tokens page - empty state
Create New API Token
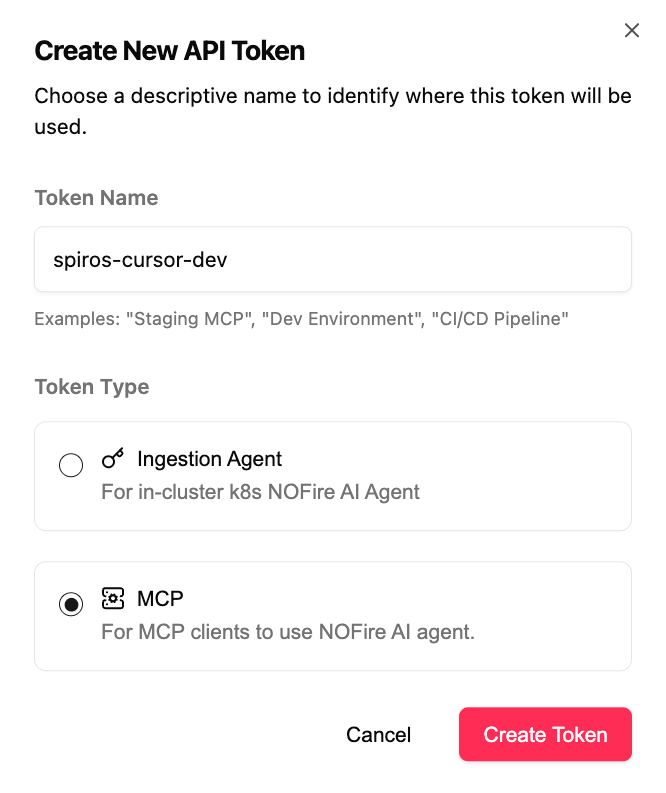
Create API Token form - Choose MCP type
- Name: Descriptive name (e.g., “john-cursor-dev”, “sarah-claude-desktop”)
- Type: Select MCP
Copy the API Token
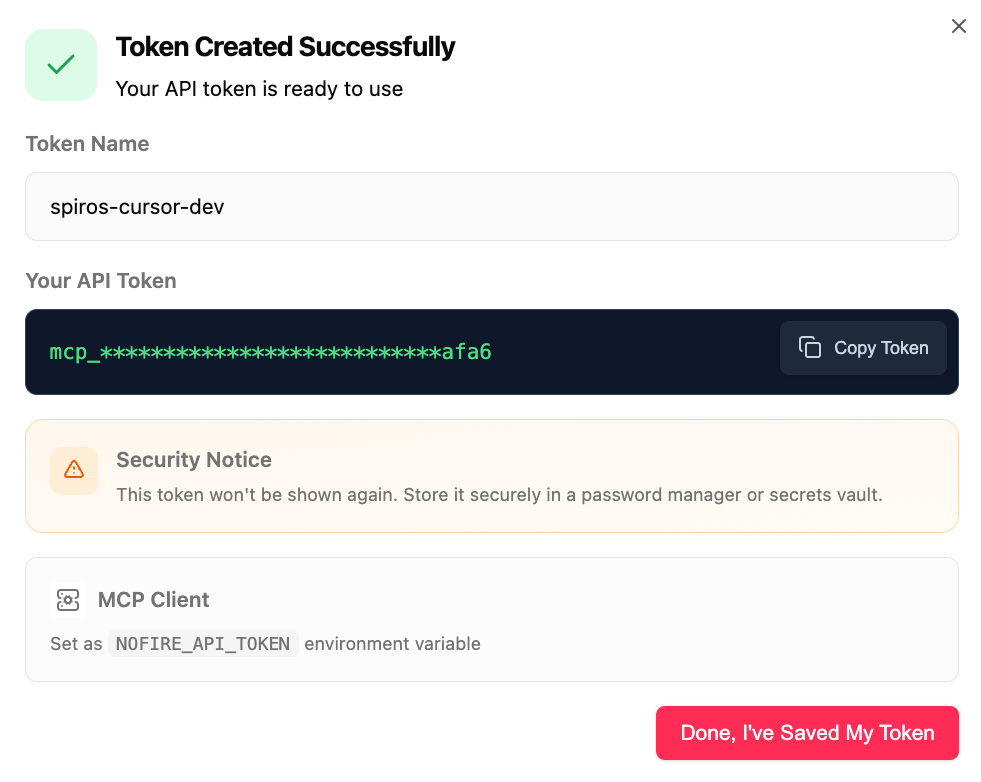
Token created successfully - Copy and save securely
Configure Your IDE
API Token Management
Viewing API Tokens
In your dashboard under Administration → API Tokens, you can see:- Key Name: The descriptive name you provided
- Key Type:
agentormcp - Status: Enabled or Disabled
- Created: When the key was generated
- Last Used: Last successful authentication
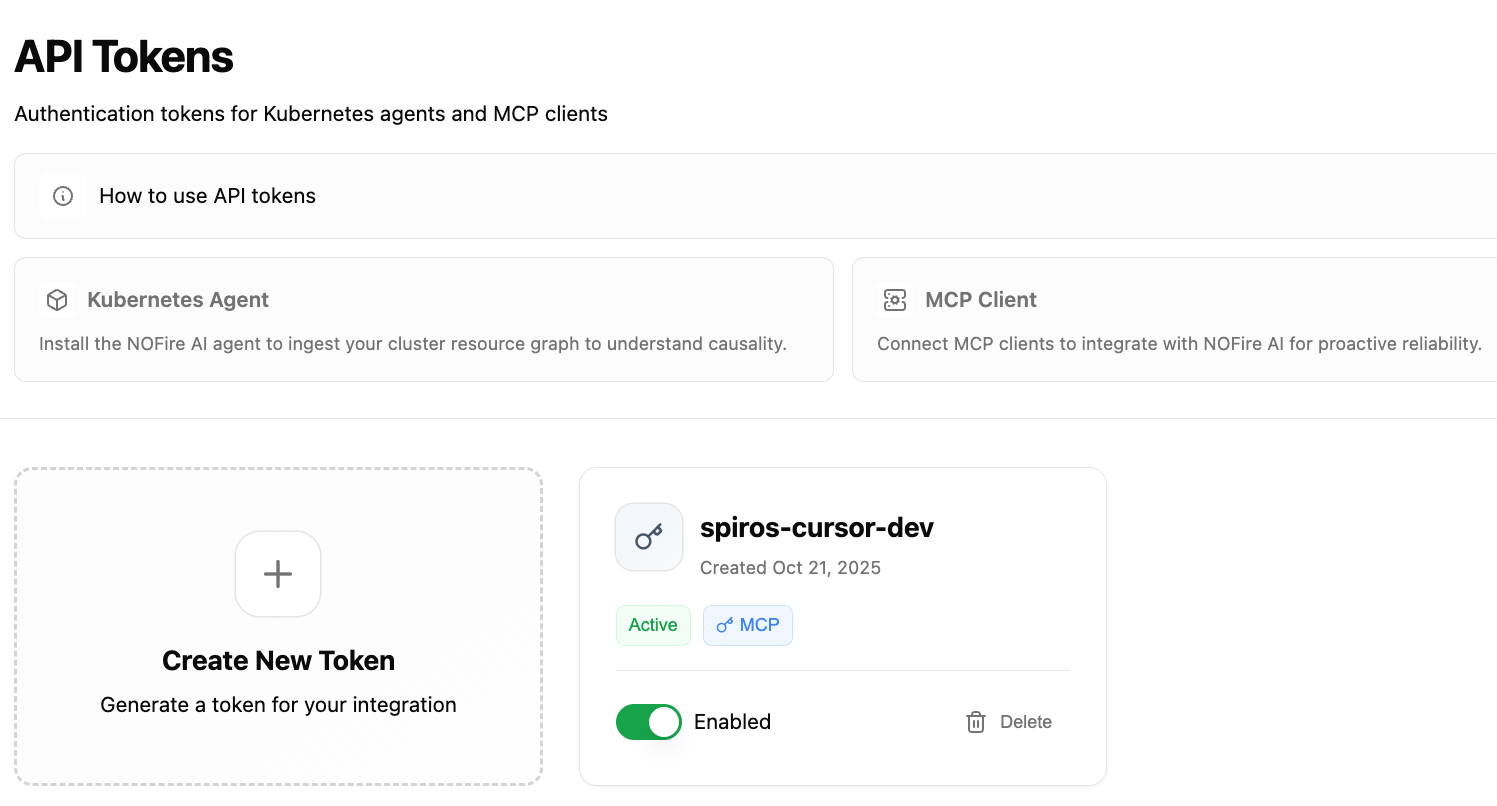
API Tokens list with token management options
Deactivating API Tokens
You can temporarily deactivate tokens without deleting them:- Go to Administration → API Tokens
- Find the key you want to deactivate
- Click the toggle to change stEnabled or Disabled**
- Employee leaving the team
- Suspicious activity detected
- Rotating keys as security practice
- Temporarily disabling integration
Deleting API Tokens
Permanently remove API tokens:- Go to Administration → API Tokens
- Click the Delete button next to the key
- Confirm deletion
- Key compromised
- Integration no longer used
- Replacing with new key
Security Best Practices
Use Separate Keys Per Developer
Use Separate Keys Per Developer
- Track individual usage
- Revoke access per person
- Audit who made what queries
Separate Keys for Different Purposes
Separate Keys for Different Purposes
- Limit blast radius of compromised keys
- Track usage by purpose
- Easier to rotate specific keys
Never Commit Keys to Git
Never Commit Keys to Git
- Git repositories
- Docker images
- Configuration files in version control
- Public documentation
- Environment variables
- Secret management systems (encrypted vaults, secret stores)
- CI/CD secret storage (GitHub Secrets, GitLab CI/CD variables)
- Local config files in
.gitignore
Rotate Keys Periodically
Rotate Keys Periodically
- Developer IDE keys: Every 6 months
- CI/CD pipeline keys: Every 3 months
- Shared automation keys: Every month
- Compromised keys: Immediately
- Generate new key with temporary name
- Update all configurations to use new key
- Test everything works
- Deactivate old key (not delete!)
- Monitor for 24-48 hours
- Delete old key if no issues
Monitor Key Usage
Monitor Key Usage
- Keys not used in 30+ days (consider deactivating)
- Unexpected usage patterns
- Failed authentication attempts
- Keys used from unusual locations
- Multiple failed authentication attempts
- API token used from new IP address
- Unusual query volume
Store Keys Securely Locally
Store Keys Securely Locally
- Use full-disk encryption
- Lock computer when away
- Use password manager for key storage
- Enable 2FA on NOFire AI dashboard
API Token Security
NOFire AI API tokens are designed with security in mind:- Unique Identifiers: Each key is cryptographically unique and securely hashed
- Type-Based Permissions: Keys have fixed permission levels based on their type (MCP tokens are always read-only)
- Account Isolation: Keys are scoped to your specific account and cannot access other accounts’ data
- Secure Storage: Keys are stored in an encrypted secret store using industry-standards.
Using Your MCP Key
Once generated, use your MCP token in your IDE configuration:For Cursor or Claude Desktop
Troubleshooting
Invalid API Token Error
Invalid API Token Error
401 Unauthorized - Invalid API tokenPossible causes:- Key was copied incorrectly (missing characters)
- Key has been deactivated or deleted
- Using wrong key type for operation
- Key has expired or been revoked
- Re-copy key from secure storage (check for spaces or line breaks)
- Verify key is active in dashboard
- Ensure you’re using an MCP token (not an agent key)
- Generate a new key if the old one is lost or compromised
Permission Denied
Permission Denied
403 Forbidden - MCP tokens are read-onlyCause: Attempting a restricted operation with an MCP tokenSolution: MCP tokens are read-only and can only query and analyze data. They cannot modify production systems, trigger deployments, or change infrastructure.Rate Limiting
Rate Limiting
429 Too Many RequestsCause: Exceeded API rate limitsCurrent limits:- 100 requests per minute per key
- 1000 requests per hour per account
- Implement exponential backoff
- Cache results when possible
- Distribute load across multiple keys
- Contact support for higher limits
FAQ
How many MCP tokens can I create?
How many MCP tokens can I create?
Do MCP tokens expire?
Do MCP tokens expire?
Can I see what my key has been used for?
Can I see what my key has been used for?
- Last used timestamp
- Total requests made
- Failed authentication attempts
Can I use one key for multiple IDEs?
Can I use one key for multiple IDEs?
- Each developer
- Each IDE/tool
- Each CI/CD pipeline
What happens if my key is compromised?
What happens if my key is compromised?
- Deactivate the compromised key in the dashboard
- Generate a new MCP token
- Update your IDE configuration with the new key
- Review usage logs for suspicious activity
- Contact [email protected] if you suspect unauthorized access
- ✅ Cannot modify infrastructure, deploy changes, or execute commands
- ⚠️ Can query service topology, dependencies, and change history
- ⚠️ Can access operational metadata (service names, deployment patterns)
- ⚠️ Could reveal architecture details to attackers
I see 'agent' keys in the dashboard. What are those?
I see 'agent' keys in the dashboard. What are those?

